The Most Vulnerable Operating System Wasn’t Windows!
Apple’s operating system is considered to be the most secure consumer operating system whether it’s Mac OS X for desktop computers or iOS for iPhones. But believe it or not, they were the most vulnerable operating systems of 2014.
Windows, which is often referred to as the most vulnerable operating system in the world and also an easy target for hackers, is not even listed on the top three vulnerable Operating Systems.
Top Vunerable OS
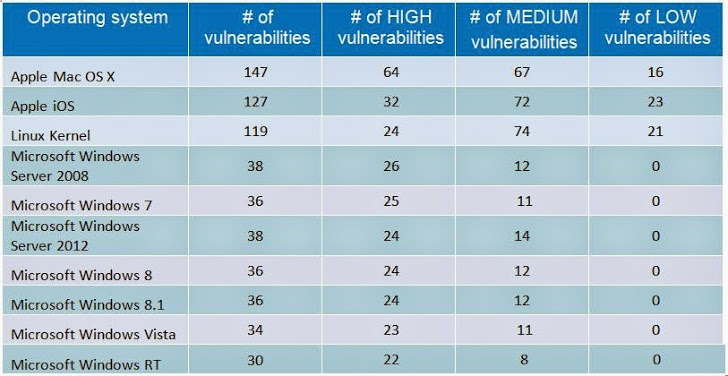
According to an analysis by the network and security solutions provider GFI, the top three most vulnerable operating system are:
- Apple’s Mac OS X
- Apple iOS
- Linux kernel
GFI analysis is based on the data from the US National Vulnerability Database (NVD), which shows that in 2014, the top three most vulnerable operating systems became so by the following number of vulnerabilities reported in their software:
- Mac OS X – Total 147 vulnerabilities were reported, 64 of which were rated as high-severity
- Apple’s iOS – Total 127 vulnerabilities were reported, 32 of which were rated as highly-severity
- Linux Kernel – Total 119 vulnerabilities were reported, 24 of which were rated as high-severity.
MAJOR VULNERABILITIES REPORTED IN 2014
The major vulnerabilities that took over the Internet in 2014 were as follows:
HEARTBLEED – A critical security vulnerability detected in OpenSSL left large numbers of cryptographic keys and private data from the most important sites and services on the Internet open to hackers. It was considered to be one of the biggest Internet threats in history.
SHELLSHOCK – A critical remotely exploitable vulnerability discovered in the widely used Linux and Unix command-line shell, known as Bash, aka the GNU Bourne Again Shell, left countless websites, servers, PCs, OS X Macs, various home routers, and many more open to cyber criminals.
Surprisingly, Microsoft’s Windows 7, 8 and 8.1 Operating Systems were the least vulnerable Operating Systems, as they fall into the bottom half of the list and rank at 5th, 7th and 8th, with 36 vulnerabilities reported in all of them.
“2014 was a tough year for Linux users from a security point of view, coupled with the fact that some of the most important security issues of the year were reported for applications that usually run on Linux systems,” explained GFI Software manager Cristian Florian.
Linux and Mac OS X Most Vulnerable OS In 2014
Windows Server 2008 was the fourth most vulnerable OS in 2014 with 38 vulnerabilities, but it isn’t a version aimed at consumers.
MOST VULNERABLE APPLICATION
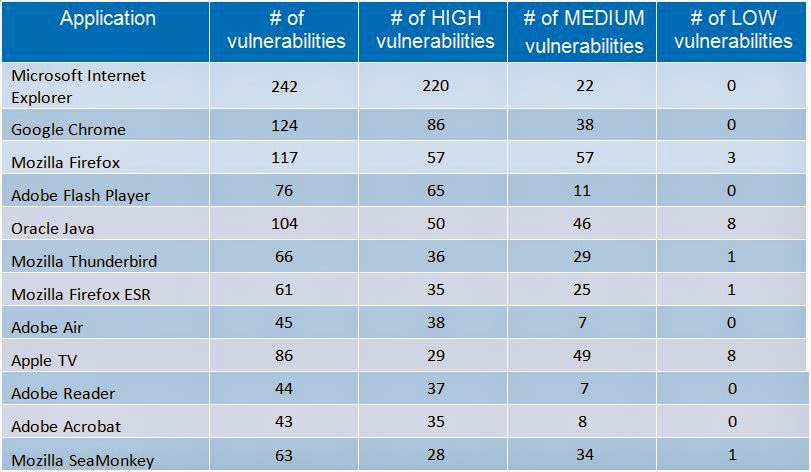
However, when it comes to applications, Microsoft came in where we thought it would, as its Internet Explorer browser lead the list with 242 total vulnerabilities, with 220 of them being rated as critical.
Obviously, this could embarrass Microsoft, as Internet Explorer has nearly twice as many security flaws than the second most vulnerable application, which was Google Chrome.
Google Chrome browser had 124 vulnerabilities reported in 2014. On the other hand, Adobe Flash Player improved last year with only 76 vulnerabilities reported.
Overall, a total of 7,038 new security vulnerabilities were added to the National Vulnerability Database (NVD) last year, which indicates that an average of 19 new security vulnerabilities were reported every day.
Out of those, 80% were reported in third-party applications, 13% in operating systems, and 4% in hardware devices.
For those who aren’t aware, NVD is the US government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP).
Thanks to GFI and “The Hacker News” for the report.